A little bit of housekeeping. The free telephone guy that I wanted to bring over made sense after a bit of investigation. Wil demonstrated some apps and web sites that basically offer this already. Free Wifi is all over the place now and these free telephone apps are starting to cash in somehow. So I apologize for the guy who is essentially, simply selling $150 smart phones that his story was incredible but it's hard not to wonder about a poster that begins "(the name of these two dudes from the Eastside) they have seen the future, and it is GOOD. Free hi speed WiFi shall set u free. Free of telephone bills forever for calls almost anywhere in Canada. Will the zeal of missionaries, they plan to spread the blessings of affordable phone and communication services ..."
Next study group (Feb. 27 2016) we will be videotaping Wil's presentation on cyber-culture's effect on society. They'll be a quick question and answer session after each ten minute segment. We will be using this for a quick video editing in Youtube primer.
Now about this week's study group; Social Media. Once upon a time someone came up with the concept of web logging. That is when one would regularly provide short blurbs about this or that and update his ideas regularly. Soon someone else called it blogging and that took off pretty good. All of sudden micro-blogging came along complete with its hash-tags and limited characters. Twit heads spewed from news and fashion and movie sources into a bewildering chorus of burbling tweets. Facebook posts and G+ posts evolved into mainstream microblog platforms; Google figuring out a decent product a bit late in the game. We didn't even bother talking about such nuisances as Instagram and Pinterest let alone contemplate anything LinkedIn to anything.
We looked at most of the pros and cons of each platform. we then experimented with creating Facebook fan pages and Google+ Pages for our Digital media study Group.
As an experiment. We wrote a post that was available in the search engine results within five seconds and ranked second on the first page mainly because the search engine recognized that our IP address just wrote it.
We discussed how important it is to establish trust with the search engine by continually offering it unique and well crafted content. This included optimization of image attributes and videos. we demonstrated how social media triggers can effect search engine rankings. Fred pointed out that Google search results often contained G+ posts in the first page of results but rarely would show a Facebook fan page equivalent.
It was noted that when working with Google products such as Blogger and Google+ that it is better to use Google's Chrome browser. Other common web browser are often limited, malfunction or even completely non-responsive to Google products.
We had our meal ticket draw and a bit of a social and it all ended rather peacefully.
Seminars and discussions about the facts, the myths and ethics questions about everything digital media and marketing. A think tank, a help centre the brainchild of the UBC Humanities 101 Community Programme, Recovery by Design Art Studio and ARA Mental Health Advocacy and Community Resources of Vancouver.
Showing posts with label Search Engines. Show all posts
Showing posts with label Search Engines. Show all posts
A Look at Email and General Online Communication Security
We held our second Digital Media and Marketing Community Study Group on January 30 2016. We had twelve participants attend the Email and
Internet Security discussion and a couple of short demonstrations.
Email Communication and Internet Security Study Group
In opening, we thanked the Salish people for use of this
beautiful land.
The session started off with a “In the News” item. Seems
like Canada’s
spy agencies are not only saving meta data but also sharing it with other spy
agencies around the world. Amanda Connolly writes in ipolitics.ca “…a
pair of reports that slammed the Communications Security Establishment for
breaking the law and sharing Canadians’ metadata …” We talked about this
for a few minutes and generally agreed that the spy agency’s claims that they
never shared the actual content of Canadians’ emails but only shared the meta
data was completely ludicrous.
We were supposed to get a presentation from Mike. He’s a
DTES techie type that offers a $150 Smartphone with free telephone service for
life. As this seemed too good to be true we invited him to give us the
presentation but he failed to show up. The facilitator said he would try to
coax the free-from-the-telephone-companies guy into coming back to the shark
tank so we could tear his scam apart. That could be interesting.
We had a brief summary of last session’s main topics and then
started into Internet Security stuff.
We talked about the panhandler from Los Angeles who started accepting credit
cards swipes on his Smartphone as a measure to counteract passersby’s claims to
only carry plastic. It’s a free app, why not. It’s just a matter of time when
someone will figure out how to capture your credit card data with a swipe app
and then industrious homeless people will be out of luck with this innovation.
One of the participants was asking about the various types
of Internet marketing methods that are currently being deployed. We narrowed it
down to search engine marketing, social media marketing, affiliate marketing
and email marketing. This study group will only focus on the search engine and
social media marketing options as the other two are becoming more obsolete each
year.
We did talk a moment about robo-calling. This can be an
effective means of communication and marketing however it comes with risks. We
learned that in Google Hangouts, users can place telephone calls anywhere
across Canada
for free. The process of making Skype or G+ Hangout telephone calls could be
automated, we concluded giving a bit of validity to our free-phone elixir
salesman.
We had a demonstration on what was meta data in both an
email message and in an HTML page. One identifies locators and users while the
other is used to give the search engine or the Internet browser instructions.
We looked at the HTML Title tag situated in the <HEAD> and was instructed
that in fact this could be the most important tag in your entire web document.
We talked about how the search engine, the operating system
and some software programs are design to collect intelligence from its users.
This data was suggested to not only be used for security reasons but was likely
for sale to advertisers in order to better target ad delivery.
We looked at how easy it was to place search engine ads on
our own web pages and to generate residual income from web traffic that choose
to go elsewhere. It was surmised that click-through fraud could easily be
perpetrated by encourage others to click ads. We examined several ways in which
web pages are intended to trick visitors into clicking through ads. We talked
about “Internet visitors”, a new IT position that was created to exclusively go
to web pages and click through advertisement. It was mentioned that most of
these fraudsters have their operations overseas but do have satellite centres
clustered throughput North America in order to
appear to be more local. Unfortunately some Internet marketers take advantage
of slave and even child labour in order to profit from click-through revenue
generation.
We went through various functions of the <HEAD> and
the <BODY> sections of web pages, looking particularly at meta, title,
link, image, paragraph and heading tags.
We talked about Google's "engineering glitch" that caused its Google Mobile to capture household wireless network passwords while in the process of simply taking pictures of houses on the street. Fred concurred that if Streetview had this technology then what the heck was the Google mobile doing in our Parliament buildings? Fred also made us aware of the revelations that Edward Snowden (NSA whistleblower) leaked regarding tech companies including Google, Yahoo and Facebook that were working closely with American spy agencies by allowing unfeathered access to their servers.
We talked about Google's "engineering glitch" that caused its Google Mobile to capture household wireless network passwords while in the process of simply taking pictures of houses on the street. Fred concurred that if Streetview had this technology then what the heck was the Google mobile doing in our Parliament buildings? Fred also made us aware of the revelations that Edward Snowden (NSA whistleblower) leaked regarding tech companies including Google, Yahoo and Facebook that were working closely with American spy agencies by allowing unfeathered access to their servers.
Wil gave a very brief glimpse into his understanding of
cyber culture and its impact on contemporary society. It was a good enough
tease for his upcoming presentation on this topic February 27, 2016.
There was a brief discussion on how the search engine now uses localization and personalization to offer a more accurate search result for its users.
There was a brief discussion on how the search engine now uses localization and personalization to offer a more accurate search result for its users.
Finally, we examined a couple of the more traditional ways
that people attempt to scam others out of money using the Internet.
The module closed with a draw for two free meals at the Evelyn
Saller Centre.
Everything SEO 101, Search and Search Engines
We held our first Digital Media and Marketing Community Study Group on January 16 2016. We had two facilitators and five participants attend the Search Engine and SEO discussion and demonstration.
Notes:
Digital Media and Marketing Study Group - Module 1
Notes:
After a brief introduction of ourselves we got right into the nitty gritty of search engines right away. We went through a brief history of search engines and took the opportunity to introduce SEO (search engine optimization 101) and the need for it when deploying an Internet marketing campaign. We went through several types of the major search engines of today: Google, Twitter, Facebook, MSN, Ebay, Yahoo, Kijiji and Craigslist. We looked at how the volume of searches is continually increasing exponentially from two hundred million a month in 1993 to the billions of searches per day we see today.
We went through some the search operators that can be used to assist in refining searches and in assessing keyphrase competitors.
We went through some the search operators that can be used to assist in refining searches and in assessing keyphrase competitors.
A lengthy discussion ensued about how to choose keyword phrases to highlight. Fred mentioned about the Adwords Keyword Planning Tool in order to locate additional relevant keyword phrases for an SEO campaign. Here are a couple of snapshots of what that looks like:
We took turns explaining our Internet ideas. They varied from one who wants to create an online newsmagazing to an engineer that wants a bit of an upgrade in the technology. One of our participants had a question regarding hiding her web pages from the search engine while using a blogspot subdomain. She cannot access the server and install a robot.txt file with instructions as to what not to crawl. We didn't have an answer at the time but in further consideration the problem could be solved by editing the template file to include a meta tag within the HEAD portion <meta name="robots" content="noindex, nofollow">.
We chatted a bit about the freedoms we have to write basically whatever we want to write.
We also talked a bit about how to emphasize keyword phrases so that the search engine knows they are important to you. Good page structure is more search engine friendly when paragraphs are separated by headings. Emphasis can be placed on words by capitalizing the first letter, using bold or italic, using the keyphrases in textual anchors, logical naming of images, videos and web pages ... using attributes to image tags. These things will all be covered again when we start getting into blogging.
Not mentioned during the group but knowledge of HTML is a definite asset when it comes to optimizing code for best search engine performance. Web pages should be validated for errors. Spelling needs to be immaculate. The better a writer a person is, the better an optimizer they'll be as the search engines value intelligently crafted and cared for content.
Fred ensured us that internal hyperlinks within your own site are just as valuable if not more so than setting about starting a link building strategy from external sources.
We had a bit of a snack and a little social time then closed up the study group around three in the afternoon. We are quite sure these first five participants will return on January 30th for the second study. Maybe some others will join in. As most of our topics are inter-related to some degree, we are just going to pick up where we left off last time.
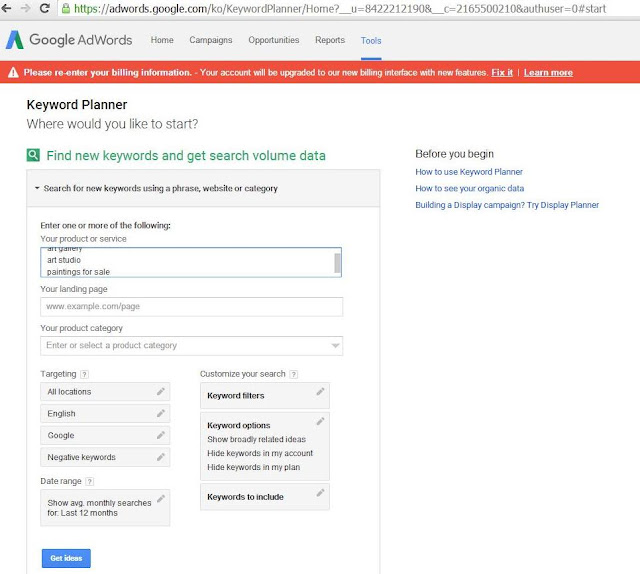 |
| type in the keyword phrase and click Get Ideas |
 |
| search frequency tests offer alternative keyphrases to consider |
We chatted a bit about the freedoms we have to write basically whatever we want to write.
We also talked a bit about how to emphasize keyword phrases so that the search engine knows they are important to you. Good page structure is more search engine friendly when paragraphs are separated by headings. Emphasis can be placed on words by capitalizing the first letter, using bold or italic, using the keyphrases in textual anchors, logical naming of images, videos and web pages ... using attributes to image tags. These things will all be covered again when we start getting into blogging.
Not mentioned during the group but knowledge of HTML is a definite asset when it comes to optimizing code for best search engine performance. Web pages should be validated for errors. Spelling needs to be immaculate. The better a writer a person is, the better an optimizer they'll be as the search engines value intelligently crafted and cared for content.
Fred ensured us that internal hyperlinks within your own site are just as valuable if not more so than setting about starting a link building strategy from external sources.
We had a bit of a snack and a little social time then closed up the study group around three in the afternoon. We are quite sure these first five participants will return on January 30th for the second study. Maybe some others will join in. As most of our topics are inter-related to some degree, we are just going to pick up where we left off last time.
Subscribe to:
Posts (Atom)